04. Firewalls
Firewalls Heading
Firewalls
ND545 C02 L02 A04 Firewalls Part 1 V2
Firewalls Notes
Firewalls are your first line of defense.
However, it's not uncommon for organizations to get complacent and treat a firewall as some magical bastion that is standing between your data and the evil outside.
In truth, at its most basic level, a firewall does exactly what you tell it to do. It allows the traffic you tell it to allow, and denies the traffic you tell it to deny. That's it.
Here are some caveats:
- If you have a misconfiguration and open too many ports the firewall isn't to blame.
- With some exceptions, most organizations don't block any outbound traffic, so if a machine reaches out to a malicious site, that traffic will be able to respond back into your network unless it is caught by another rule.
Troubleshooting Tip
While it was in the video, it's worth mentioning again. Most firewalls process their ruleset in order from top to bottom. Once a condition is met, i.e. a rule is processed, the firewall stops looking for other rules and executes the action.
So if your traffic isn't behaving the way you anticipate, check to be sure that a rule above the one you just made isn't affecting your traffic.
Firewalls Image
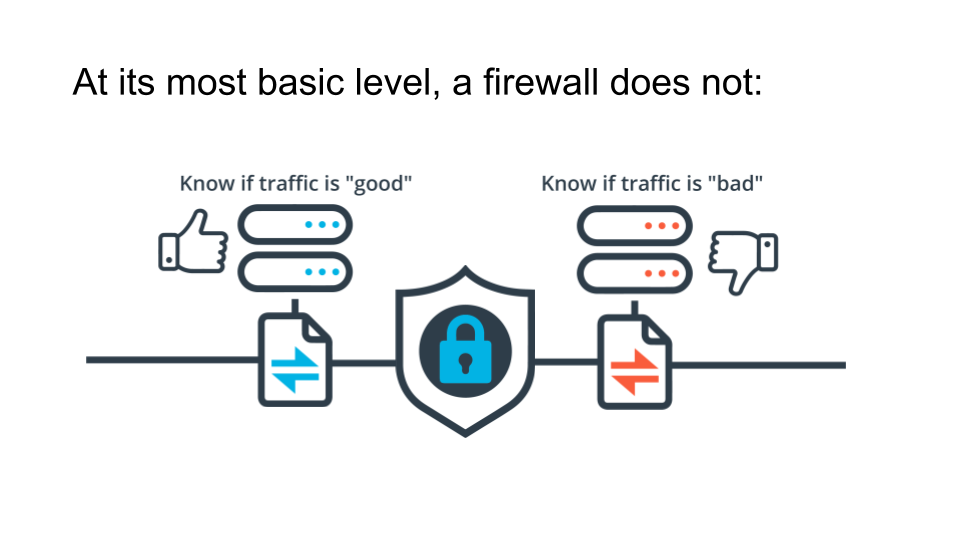
This can't be stressed enough, the firewall does exactly what you tell it to do. Check your work!
Beyond Basic
Next Gen Firewall: is a network security device that provides capabilities beyond a traditional, stateful firewall. While a traditional firewall typically provides stateful inspection of incoming and outgoing network traffic, a next-generation firewall includes additional features like application awareness and control, integrated intrusion prevention, and cloud-delivered threat intelligence.
NGFW is perfect for automation. They allow you to subscribe to automatic threat lists such as IP and URL blacklists that are updated dynamically based on intelligence.
ND545 C02 L02 A04 Firewalls Part 2
Firewall Rules
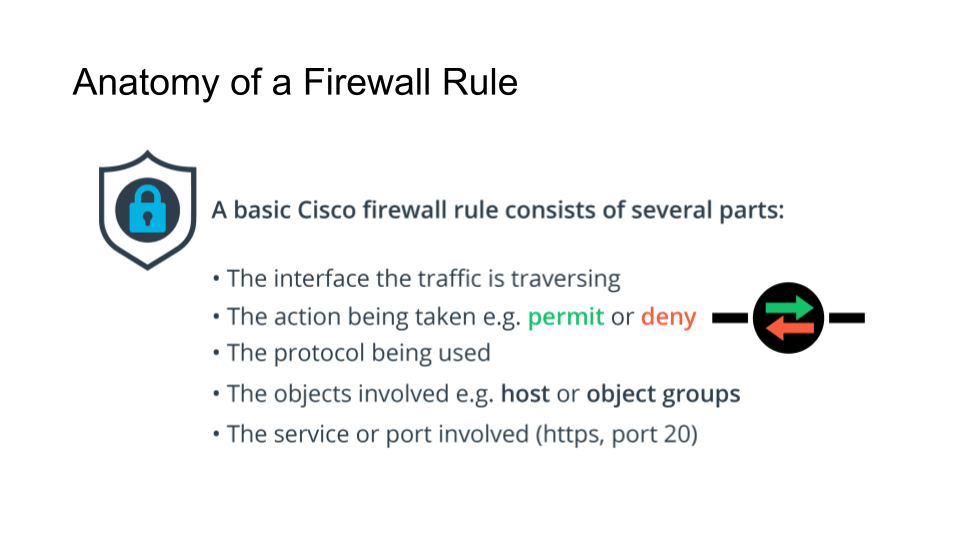
Anatomy of a Cisco Firewall Rule
The above example was for a basic Cisco firewall rule. The rules do get more complex and vary from vendor to vendor.
However the basic flow is consistent, you'll have
- the interface being traversed
- whether the traffic is allowed or denied
- the source IP
- the destination IP
- the port or service being used.
The NGFW will use the application instead of a port, for example, SSH instead of TCP-22 as the built-in intelligence can detect if it is indeed SSH traffic and not just TCP-22 traffic.
Firewall Rule Walkthrough
ND545 C02 L02 A05 Firewalls Walkthrough
Firewalls Further Research